
With the RESTRICT Act possibly impacting the use of VPNs, mainly commercial vendors, you can run your own for just a couple dollars a month from a VPS provider being cheaper than most of the commercial vendors. The downsides are you’re not masking your activity with a lot of other users, and you won’t have access to different servers distributed around the world. But then some VPN companies are less than transparent, being bought up by people linked to intelligence services, and can you really trust third parties or that you won’t get wrapped up with others using the VPN for illegal or nefarious activity? Consequently, your own VPN will conceal your IP address and give you insulation from ISP snooping, and it’s not too difficult to setup. And an added benefit is you can run a Pi-hole/Unbound DNS server along with your VPN for advertisement, telemetry, and malware address filtering.
To get started you’ll want to install a Debian server on your VPS provider (like Digital Ocean, Vultr, Linode…). From there you can run the install script for Pihole and follow their instructions:
https://docs.pi-hole.net/main/basic-install/
Next follow the instructions for Unbound which will act as your recursive DNS server, so instead of using another provider like Google or OpenDNS, you’ll have a recursive DNS server that will search out the authoritative DNS provider for the site you’re trying to access. This will protect you from DNS injection attacks or tracking that might be happening with the big DNS servers, megacorps.
https://docs.pi-hole.net/guides/dns/unbound/
After your Pi-hole/Unbound server is all setup, it’s time to install the VPN. PiVPN is basically an install script that will easily help you setup the VPN and use the Pi-hole/Unbound server. In addition to the install functionality, you’ll also have a handy CLI tool to manage your VPN, show QR codes for access, add remove accounts…. I’ll recommend the Wireguard VPN as it’s built into the Linux kernel, smaller code base, more efficient, and well audited for security.
https://docs.pivpn.io/install/
A quick list of pivpn commands for managing your VPN:
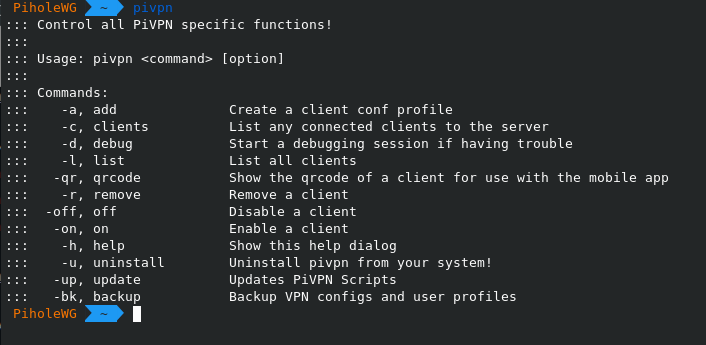
As this will be a server on the internet you’ll want to setup your firewall, and ufw is the easiest to use but you’ll have to jump through a couple hoops later which is still better than dealing with iptables (you might be able to use your providers web firewall application). You’ll need to make sure your SSH and VPN ports are open. For quickly setting up Pi-hole I use one of my existing server configurations with all the lists to upload through the Pi-hole web interface and then lock it down later. You can also lock access down to your home IP address using ufw. And Ubuntu is based on Debian, so these guides will work with Debian.
https://www.digitalocean.com/community/tutorials/how-to-set-up-a-firewall-with-ufw-on-ubuntu-20-04
And to get the traffic forwarding through the server with ufw you’ll need the following tweaks.
Client Applications
The Wireguard app on Android:
https://play.google.com/store/apps/details?id=com.wireguard.android
The Wireguard app for IOS:
https://apps.apple.com/us/app/wireguard/id1441195209
Wireguard for Windows:
https://www.wireguard.com/install/
For Linux you should just need to install wireguard-tools from your distribution software management tool. You then use pivpn -a to add accounts to access the VPN on the server. You can use pivpn -qr to show the QR code for your phone or device equipped with camera, or go into the configs directory in the home directory to get the configuraton you can use with a Linux or Windows client. You can also just scp or rsync the file to your machine, and then copy to the /etc/wireguard directory and rename to the interface you’d like to use, e.g. wg0.
One additional tweak if you don’t want to SSH in and manage the server, install unattended-upgrades so the software stays up to date. So not only will you have your own VPN server, you’ll learn a little as you set it up and manage it, and you can trust it isn’t spying on you or flagging you for interdiction because of the RESTRICT Act.