Before you discount using Tor as the western media propaganda would make you think it’s for hackers and the dark web, Tor was actually created by the U.S. Naval Research Lab for their agents, press, people fighting for human rights, and whistleblowers. Primarily the use case was for these entities outside the country to protect themselves from oppressive governments, spy agencies, criminal corporations… who would object to their activity and possibly put them in danger. Consequently, Tor was released as an open source project and anyone can use it, run servers, or hidden services enjoying the same privacy benefits.
Tor stands for The Onion Routing. There are two parts to Tor, onion routing to regular websites going through 3 servers located around the world, and hidden services that join the Tor network and are hidden by the same level of 3 servers connecting to the surfer’s 3 servers for a total of 6 server hops around the world. Some large corporate entities also provide hidden service addresses for people to privately use their sites outside of prying eyes. And the connection is encrypted at every layer and server giving you privacy protection per layer. So the entry server knows who you are, but can’t determine where you come out the last server or which sites you’re visiting, and the last server has no idea who you are or where you are in the world. And the middle server can’t see anything other than what servers it’s relaying. Given that the hops go around the world, it limits any one government from being able to track your activity. And the servers are provided by people that value the Tor service and privacy, and years ago after the Snowden revelations I had run a couple servers overseas for a few years. Moreover, there are built in methods for rooting out bad actors that might try to run servers to spy on users. And as you can see below, there is a button if you want to generate a new path, or circuit of three servers.

And the version 3 hidden service protocol uses six servers, with the three being used by the hidden service being hidden from the surfing user.
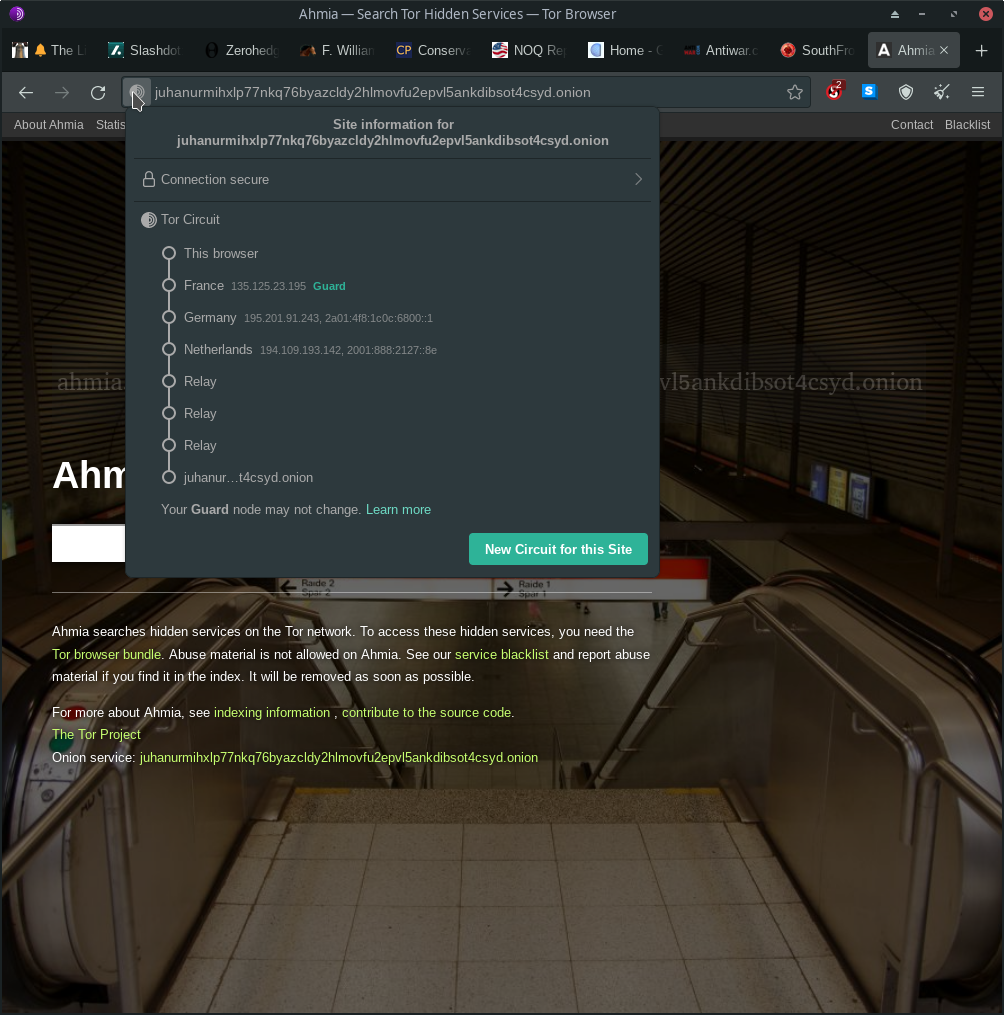
A couple things to consider when using the Tor Browser, don’t change your screen size. Browser fingerprinting is a way that sites track users, so if you change the default browser size you’re differentiating yourself from other Tor Browser users who you want to blend in with. Also, I change the default security setting to limit what JavaScript code is downloaded and run inside my browser which is another way they try to identify and track you as a user.

And from there you’ll need to right click on the toolbar menu and select Customize Toolbar in order drag the NoScript plugin to be visible in the toolbar, S with red question mark.
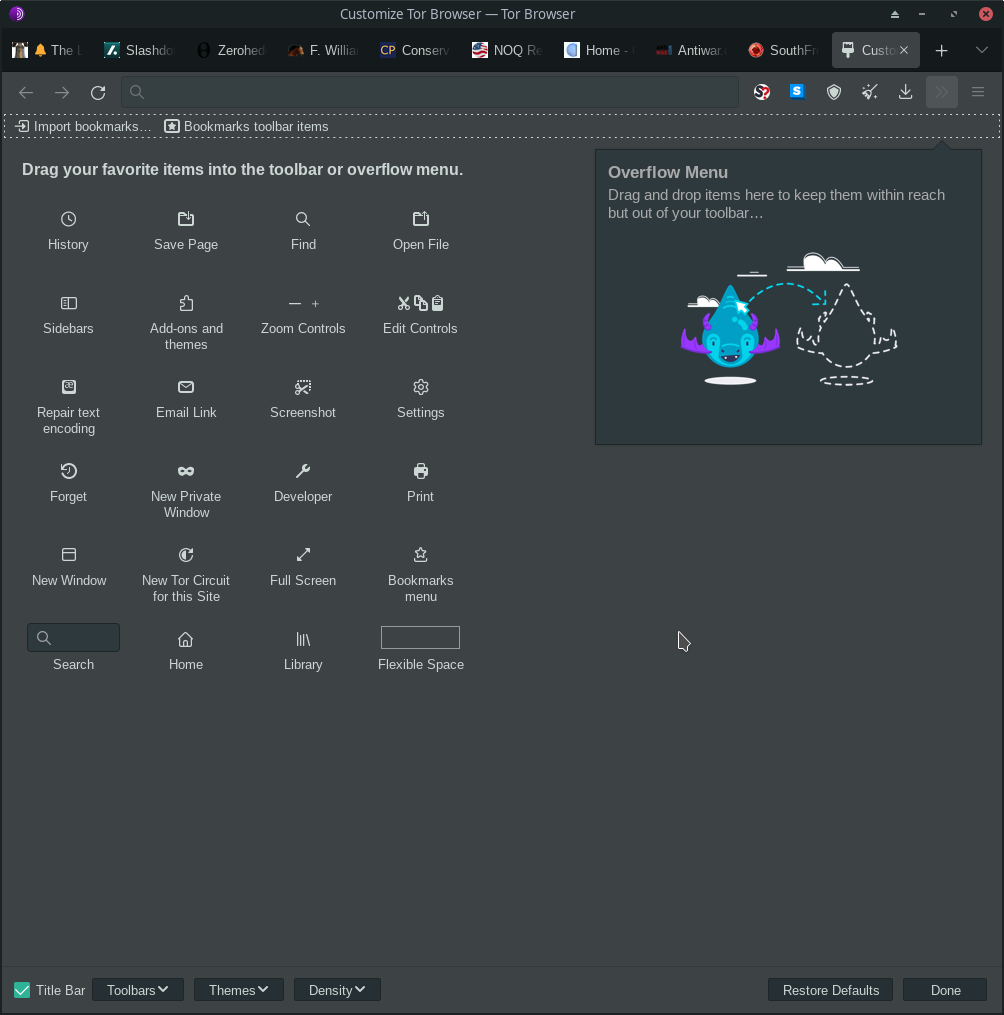
So when you don’t have functionality on certain sites you’ll need to click on that NoScript plugin and enable javaScript as needed. Better to control what sites get to run code in your browser on your machine than go with the default.
If you would ever need to use Tor Browser in a real situation, human rights, whistleblowing…. make sure you read how Tor works and follow best practices to protect yourself. You might want to think about a bootable flash drive with a basic Linux distribution that you could use instead of your main computer OS to further protect yourself as well as investigating public/private key cryptography like GnuPG to further protect your correspondence. There is a special Tails distribution of Linux made just for this and worth investigating, but there are a few other choices as well.
https://www.debugpoint.com/2022/04/privacy-linux-distributions-2022/