I’d been running my own VPS VPN server for quite a while since there were a lot of stories of these suspicious VPN companies consolidating with one connected to intelligence. And at the end of the day you’re trusting the companies to be honest when it comes to not keeping logs, and many track you with email address or other personal information. But the video in this post got me to take a look at Mullvad VPN, and having finally tried them out today, I’ve been impressed. The main reason to use a VPN is to just protect your activity from your ISP tracking you and selling your activity as well as protecting you when on open WiFi networks like at restaurants or coffee shops. The advantage to a VPN service is that they have many servers spread around the world and you can easily select them through their application which can be handy for escaping geofences to access content from streaming services in other countries. Consequently, the screen shots are from the Linux application which seems to mimic the smartphone application look and feel.
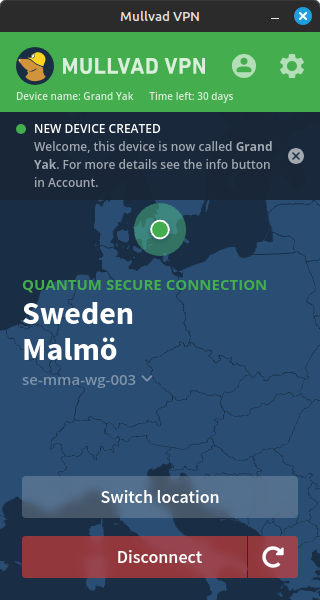
To setup the service you generate a unique number ID and then you can pay with cryptocurrency (I used Bitcoin but Monero which is a privacy focused Cryptocurrency can be used), but you can also use prepaid credit cards or even mail cash to them directly referencing that unique number. You use the number to login to the service with no password. And they have apps that are open source which support all the major operating systems even with their own repo for Debian based GNU/Linux based distributions. And the app has a lot of configuration options even with DNS blocking options that so far seem to be as good as my own Pi-Hole implementation.
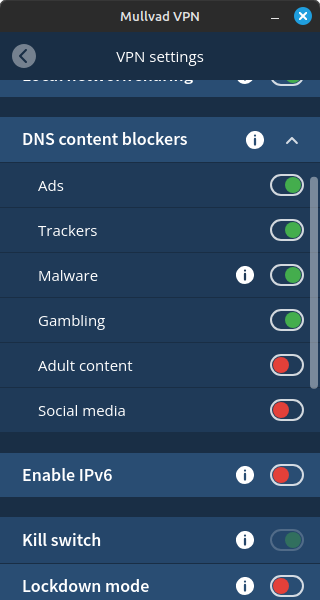
I don’t go to adult content sites, but I’m just not sure how aggressive that blocklist is or the social media one. According to their website the adult content blocking is to help those who might have an addiction and you can access their list online at Github.
Aiding to break habits: Gambling and Adult content DNS blocking
July 11, 2022 Features
We have expanded our DNS blocking service with Gambling and Adult content filters!
In addition to our Advertising, Tracker, and Malware lists, we have adding 2 more options: Blocks for adult content and gambling websites. Now available in version 2022.2! Update: Corrected iOS information.
These are based on lists that are readily available and viewable via our Github page.
Now available everywhere: Blocking adult content and gambling websites
This service is an extension to our other blocking services, where we prevent known websites that serve adult content and gambling from displaying content. These features can be used alongside our advertising, tracker and malware website blocking features, and can be enabled either via toggles available in our desktop and iOS apps or via a custom DNS entry if you are on Android, or are using our service via a configuration file.
These are the first iterations of these blocks, so they may not be perfect. We will improve them over time.
They’ve also added a switch for adding another server hop if you want more protection, though this could add latency, and if you want more you could use Tor with three server hops. And there is an obfuscation feature that makes all the packets the same size to prevent traffic analysis, Defense against AI Traffic Analysis or DAITA. Also, they have a blog post about their third audit included in full at bottom, and they use a scaled down kernel and run within ram as well. And the Swedish government tried to execute a search warrant against them to seize computers, but once informed they contained no customer information they had to leave without them according to Swedish law.
Mullvad VPN was subject to a search warrant. Customer data not compromised
April 20, 2023 News
On April 18 at least six police officers from the National Operations Department (NOA) of the Swedish Police visited the Mullvad VPN office in Gothenburg with a search warrant.
They intended to seize computers with customer data.In line with our policies such customer data did not exist. We argued they had no reason to expect to find what they were looking for and any seizures would therefore be illegal under Swedish law. After demonstrating that this is indeed how our service works and them consulting the prosecutor they left without taking anything and without any customer information.
If they had taken something that would not have given them access to any customer information.
Mullvad have been operating our VPN service for over 14 years. This is the first time our offices have been visited with a search warrant.
So far, this looks like a trustworthy VPN provider. Consequently, I’m not doing anything criminal to where I need strict protection, but with the UN agreement pushing the globalist agenda with a great desire to crackdown on internet privacy and “disinformation”, that could all be changing soon. As when they talk about misinformation or disinformation, they really mean someone telling the truth counteracting theirs. As today, government officials are the worst offenders for telling egregious lies and acting against their populations, while complaining about people not trusting them. And the benefit of using a commercial service like this compared to my own server is that I can blend my activity in with many others, as my own personal VPN was good at protecting me from my ISP, but the government could easily track my activity online. And it seems another benefit is I can access some sites that blocked my VPS provider’s IP addresses, especially good for Reddit which is useful for solving tech issues. So if you’re not using a VPN, you might check out Mullvad VPN.
https://mullvad.net/en/blog/infrastructure-audit-completed-by-radically-open-security
Infrastructure audit completed by Radically Open Security
August 9, 2023 External audits Security
We tasked the Netherlands based security firm Radically Open Security (RoS) with performing the third audit towards our VPN infrastructure.
We asked them to focus solely on VPN servers that run from RAM, one OpenVPN and one WireGuard server.
We invite you to read the final report of our third security audit, concluded in mid-June 2023, with many fixes deployed late June 2023. Further re-tests and a verification pass was performed during July.
RoS discovered a number of new findings, and we would like to thank them for their thorough and detailed report. They stated , amongst other things that: that whilst they found some issues, that: “The Mullvad VPN relays which were the subject of this test showed a mature architecture…” and “During the test we found no logging of user activity data..”
We gave RoS full SSH access to two (2) VPN servers that were running from RAM, using our latest slimmed down Linux kernel (6.3.2) and customised Ubuntu 22.04 LTS based OS. These servers were deployed as though they were to be production customer-facing servers, however these servers have never been utilised as such.
We asked them to verify:
- Security and set up of servers internally
- Security and set up of servers externally
- Whether or not we log customer activity
RoS also asked whether they should investigate the source code of various binaries running on our systems, or whether they should take into consideration the hardware-level security. We declined both offers, stating that this is to be considered an “after the system is running and in-use by customers” audit.
Overview of findings
- Radically Open Security found no information leakage or logging of customer data
- RoS discovered 1 High, 6 Elevated, 4 Moderate, 10 Low and 4 info-severity issues during this penetration test.
Key takeaway: Our VPN infrastructure has been audited for the third time.
Miscellaneous issues of interest
MLL-024 Production multihop traffic on test system (High)
To quote RoS: “Impact – Production user traffic is visible to pentest users.”
Our comments:
RoS were given production-like servers, provisioned and deployed like all other customer facing servers. The difference between these and the rest of our fleet is that they have never been made available for customers to connect, they were not advertised in our server list, and not offered up to users. However, as these servers are connected to our WireGuard multihop functionality, any customer scanning for IPs can send traffic though them whilst connected to another VPN server using a SOCKS5 proxy, as there is nothing blocking it.
In what RoS discovered there was only the IP from the WireGuard internal interface. This interface is only available to SOCKS5 multihop traffic, so it would be the entry WireGuard server.
Without providing RoS with production servers the audit would not have been valid as a production server audit, and there would have been no way to prevent customer traffic from being visible on the servers.
MLL-019 – LPE to root using systemd timers and insecure directory permissions (Elevated)
To quote RoS: “Low-privileged system accounts can elevate their privileges to root by manipulating systemd timer script content.”
Our comments:
It became obvious after consulting with RoS that the primary issue here is the use of nested home directories, and the addition of administrator users being part of the mad group.
The usage of the nested /home/mad directory structure is a legacy remnant of pre-RAM VPN servers, which is going to be removed in the upcoming updates to our infrastructure. In the short-term we have removed all administrator users from being part of the mad group, but we have also moved all related scripts to /opt/local_checks which RoS acknowledged as resolving the issue.
MLL-045 — Administrator access to production machines (Moderate)
To quote RoS: “VPN servers accept remote logins from administrators, who technically have the ability to tap into production users’ VPN traffic”
Our comments:
We have been aware of this issue for some time, and conversing with RoS only confirmed our plans to implement such measures:
- Implement a method by which unauthorised logins can be auditable, and add a log of all the commands (without arguments) used on these servers. We are implementing such a system.
- Remove support for SSH entirely, this would mean that even administrators could not enable logging of customer traffic, since no access is enabled over SSH. We are investigating such a system, though this will take more time to perform correctly.
MLL-016 – Telegraf password shared across servers (low)
To quote RoS: “Shared Influx database credentials used by Telegraf across VPN servers allows manipulation of global server metrics, such as CPU and disk usage or network metrics.”
Our comments:
We deemed the best course of action here to implement client certificates for authentication using the PKI infrastructure available within Hashicorp Vault. This has now been implemented, and we will investigate the use of such certificates in other places across our infrastructure.
—
There are more changes to be deployed in the near future, and the listed fixes are examples of the most interesting issues that Radically Open Security found.
For the universal right to privacy,
Mullvad