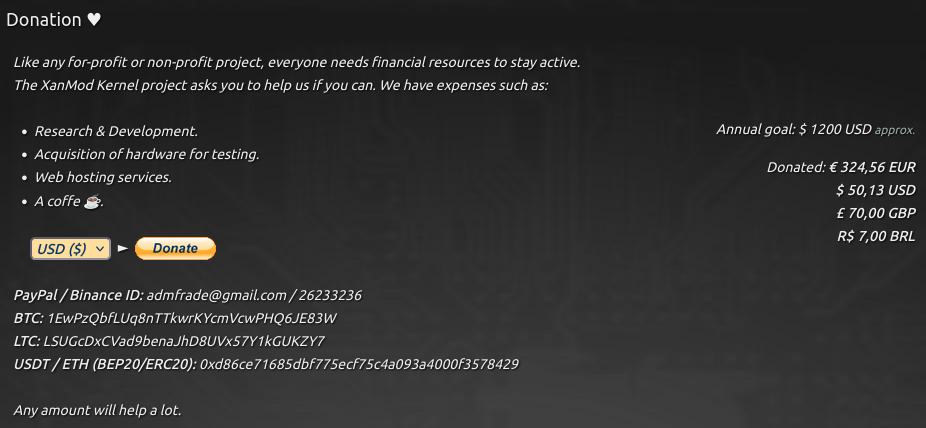
(Headline article below) This was due to the GiveWP plugin which was putting email addresses in the source code of the webpage to be harvested. And they were slow to correct and fix the bug, as I originally saw this reported by the Corbett Report. You’d have to think a deliberate attempt to identify people that donate to a lot of websites. Now I’ve donated to Pi-Hole before using Bitcoin, which for me today is the only way I donate to projects I want to support. All this requires is a Bitcoin address to be posted on the website. But the Pi-Hole project uses Coinbase (trash), and it looks like the only way you can contribute through Coinbase is by linking with a wallet which isn’t necessary, and seems to be a way of identifying you and your wallet for KYC/AML. So it doesn’t look like I’ll be donating to Pi-Hole again anytime soon. And a lot of projects don’t offer a way of contributing with cryptocurrencies. Consequently, I’ve closed my PayPal account when it came to light they could fine you, taking money directly out of your bank account, and even wanted to expand that ability for your social media posts at one time (they backtracked after mass account closures). So for online transactions, I create virtual credit cards, but as a general rule I don’t do that for donations. Below, I’ll include a screenshot of how this should be done as exemplified by the Xanmod Kernel project, who take direct cryptocurrency donations including Bitcoin (BTC), Litecoin (LTC) and Ethereum (ETH)… And the beauty of cryptocurrency payments is that it’s anonymous and you don’t have to provide personal information, with Monero being the best option for total anonymity. And using cryptocurrency is so much faster and easier than any other method.
By Sergiu Gatlan

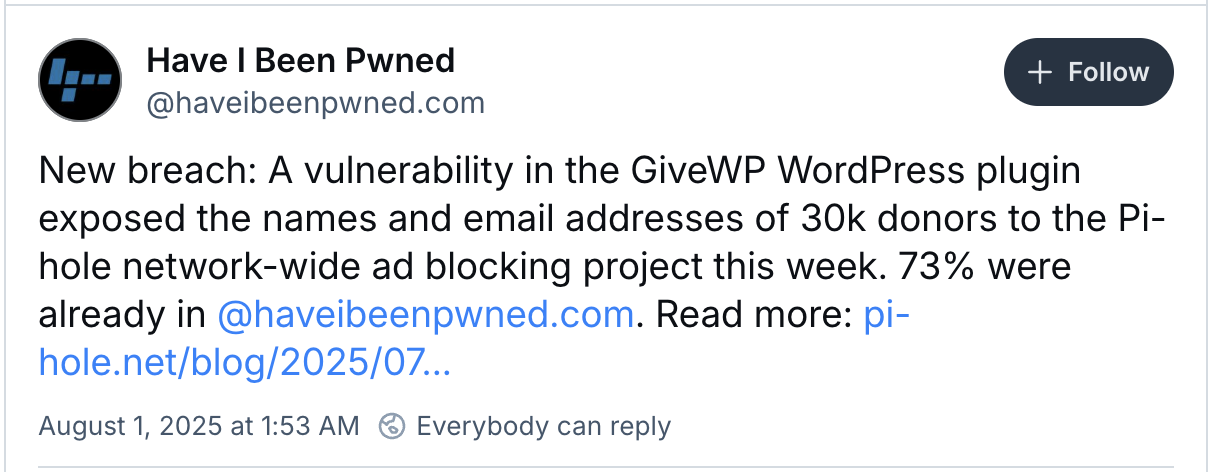
Pi-hole, a popular network-level ad-blocker, has disclosed that donor names and email addresses were exposed through a security vulnerability in the GiveWP WordPress donation plugin.
Pi-hole acts as a DNS sinkhole, filtering out unwanted content before it reaches the users’ devices. While initially designed to run on Raspberry Pi single-board computers, it now supports various Linux systems on dedicated hardware or virtual machines.
The organization stated that they first learned of the incident on Monday, July 28, after donors began reporting that they were receiving suspicious emails at addresses used exclusively for donations.
As explained in a Friday post-mortem, the breach affected users who donated through the Pi-hole website’s donation form to support development, exposing personal information that was visible to anyone who viewed the webpage’s source code due to a GiveWP security flaw.
The vulnerability stemmed from GiveWP, a WordPress plugin used to process donations on the Pi-hole website. The plugin inadvertently made donor information publicly accessible without requiring authentication or special access privileges.
While Pi-hole didn’t disclose the number of affected customers, the ‘Have I Been Pwned’ data breach notification service added the Pi-hole breach, saying that it impacted almost 30,000 donors, with 73% of the exposed records already in its database.
No financial information exposed
Pi-hole added that no donor financial data was compromised, as credit card information and other payment details are handled directly by Stripe and PayPal. It also clarified that the Pi-hole software product itself was not affected in any way.
“We make it clear in the donation form that we don’t even require a valid name or email address, it’s purely for users to see and manage their donations,” Pi-hole said. “It is also important to note that Pi-hole the product is categorically not the subject of this breach. There is no action needed from users with a Pi-hole installed on their network.”
Although GiveWP released a patch within hours of the vulnerability being reported on GitHub, Pi-hole criticized the plugin developer’s response, citing a 17.5-hour delay before notifying users and what it described as insufficient acknowledgment of the security flaw’s potential impact on donor names and email addresses.
Pi-hole apologized to affected donors and acknowledged potential reputation damage stemming from this security incident, saying that while the vulnerability was unforeseeable, they accept accountability for the resulting data breach.
“The names and email addresses of anyone that had ever donated via our donation page was there for the entire world to see (provided they were savvy enough to right click->View page source). Within a couple of hours of this report, they had patched the bad code and released 4.6.1,” Pi-hole added in a blog post analyzing the incident.
“We take full responsibility for the software we deploy. We placed our trust in a widely-used plugin, and that trust was broken.”